Introduction
The use of network scanners with a graphical user interface (GUI) has been observed in a number of former IR engagements conducted by the CSIRT Airbus Protect.
Indeed, Ransomware and Advanced Persistent Threat (APT) operators often use tools like GUI network scanners as part of their techniques.
By using network scanners, operators can map the network, identify interesting targets and plan their attack strategy while minimizing the chances of being detected. This discovery phase is important in the case of an intrusion, as it enables the proper deployment of the subsequent steps in the cyber kill chain.
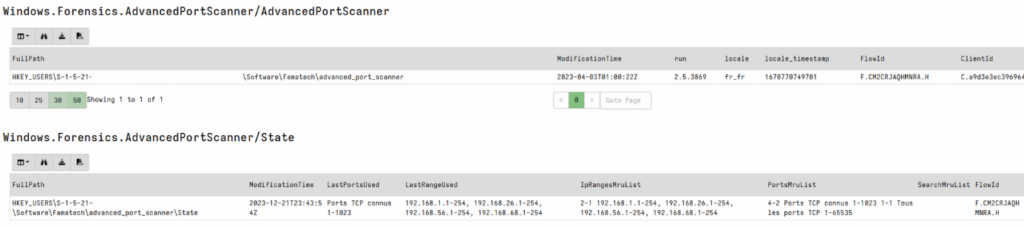
In this article, we will study three GUI-based network scanners: NetScan, Angry IP Scanner & Advanced Port Scanner, with the aim of discovering forensics artifacts. The focus will be on the type of data they generate and how to exploit this data to find out how these tools have been used on an infrastructure. This is by no means a detection approach, as is sometimes the case with NIDS.
Once these artifacts have been identified, the next step will be to effectively leverage them. To this end, we will be developing modules for Velociraptor, a tool used for digital forensics and incident response (DFIR). These modules, called Artefact by this solution, will be designed to automate the collection and the analysis of data generated by network scanners, facilitating more efficient and thorough forensics investigation at scale.
Digital forensics traces research methodology
In our approach to tracking a program’s execution on a system, we use Procmon from the Sysinternals suite. We will be focusing on all the actions of a particular program. To render our analysis more precise, we specifically filter for the operations CreateFile and RegCreateKey. These filters allow to see when a program creates or opens files and when it creates registry keys.

By doing this, we get a clear picture of how the program interacts with the system, especially in terms of file and registry modifications.
SoftPerfect Network Scanner (NetScan)
SoftPerfect Network Scanner, also known as NetScan, is a multifunctional network scanning tool that detects devices and open ports on a network, identifies file shares, provides IP configuration details, integrates security features, has an intuitive graphical user interface, enables report generation and data export, supports SNMP protocol and offers scripting options for automating network scanning tasks.
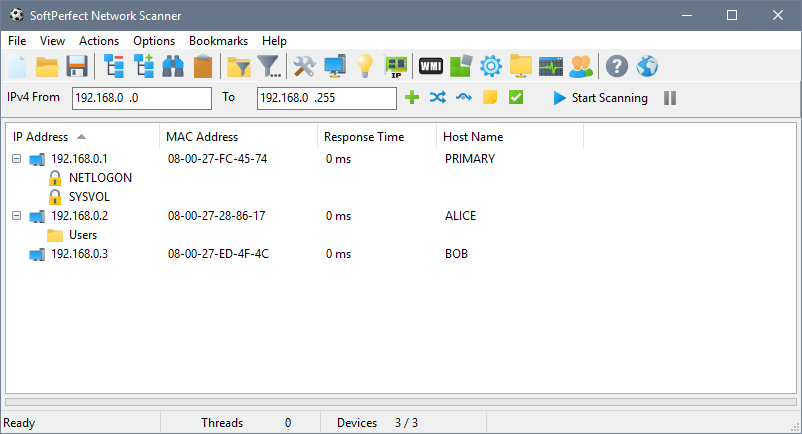
Artifacts discovered
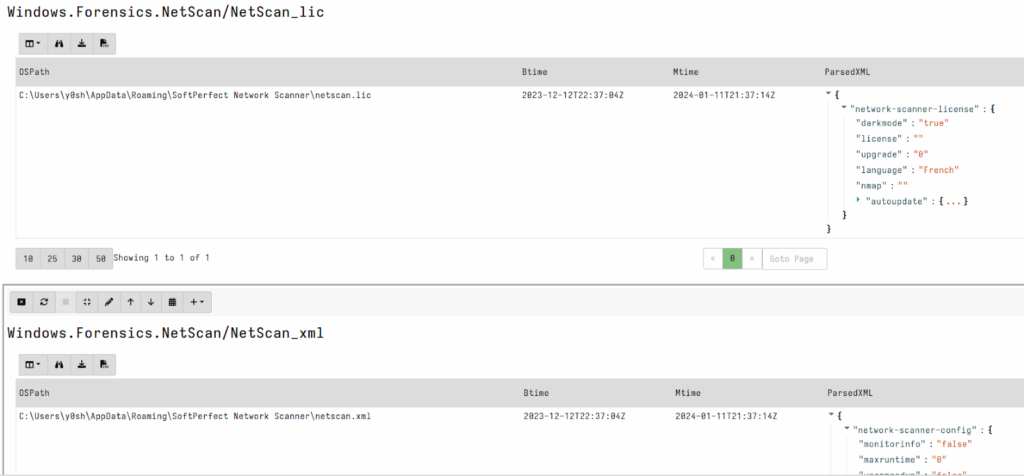
netscan.lic
This file serves as the license file used to determine whether the application has a valid purchased license or is available for free use. It is formatted as an XML file and contains information related to the program’s graphical user interface language configuration and license details, including the license name. In the case of the portable version, this file is located in the current usage directory on the filesystem. For the system-installed version, it can be found in `C:UsersCURRENTUSERAppDataRoamingSoftPerfect Network Scanner`.
Here’s an example of a netscan.lic content:
 Cybersecurity
Cybersecurity