What happened to the NHS a year ago? Let’s find out with Gareth, CTI & Vulnerability Lead at Airbus Protect
Introduction to NHS Ransomware Attack
A year has passed since the NHS fell victim to a further major ransomware attack which saw their critical NHS 111 service being taken offline alongside management systems for GP surgeries, care homes, and mental health services being affected. The largest system of which supported the care of approximately 40 million patients. Since then the healthcare industry has still been a common target for ransomware, with the NHS Trust confirming they were affected by a ransomware attack in June 2023. Just some of the reasons the healthcare services are targeted are due to their integral function to society, the sensitive data their systems hold and their increase in IoT adaptation. Following on from the incident and witnessing how cyber attacks can have devastating impacts on critical infrastructure, it is essential to continuously assess the current and ever-changing threat landscape to proactively defend and recover from future incidents. Therefore, we are going to take a further look at some of the trends seen in the cyber attack surface, what some of the challenges being faced are, and what we can do to mitigate and reduce our overall cyber risk.
Cyber Threat Trends
Ransomware as a Service
Ransomware as a service (RaaS) is a threat that has steadily been growing over the past few years and shows no sign of slowing down. As ransom demands, and subsequent payments steadily rise year on year, RaaS kits become much more attractive to potential cybercriminals. RaaS allows lower skilled threat actors to purchase a fully fledged commodity ransomware, ready to deploy in seconds. A highly prevalent example of this is Lockbit3, an affiliate ransomware, with a count of more than 570 victims as of July 2023. This commonly results in parts or whole organisations coming to a standstill during these attacks due to their systems becoming inaccessible until the demands of an attacker are met, or sensitive data is made publically available if payment is not made. Both result in on-going impacts including reputational and financial damages to recover from. This also reflects the overall trend of ransomware attacks as a whole rising each year, with roughly 3,070 ransomware victims in 2022; whilst in 2023 to date there have already been over 2,970 reported victims this year.
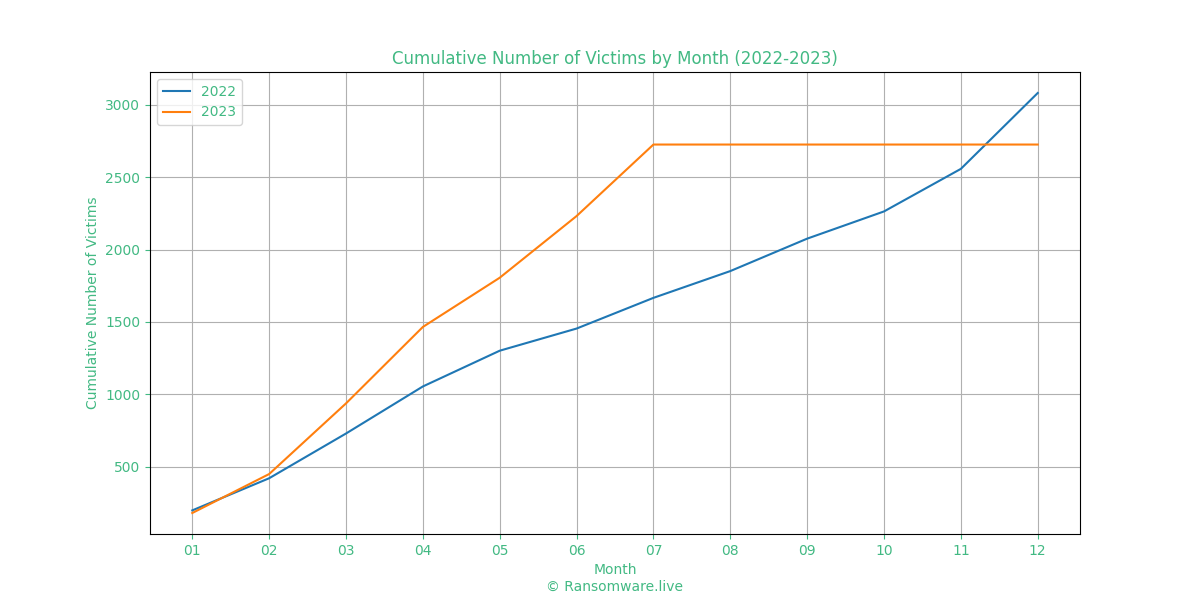
Table 1 – Ransomware Activity – https://www.ransomware.live/#/stats
Accurate as of July 2023, Ransomware.live indicated that the projected 2023 victim total is set to eclipse that of 2022.
Artificial Intelligence
Another recent threat seen throughout the year is the prevalence of Artificial Intelligence (AI) and Large Language Models (LLM) in the facilitation of cyber attacks. Commonplace, well-known models such as OpenAI’s ‘ChatGPT’ have been reportedly used to generate convincing content that can be utilised in cyber attacks, despite the best efforts of OpenAI to restrict the malicious usage of the platform. However, in the wake of ChatGPT’s huge commercial success, malicious LLMs, such as WormGPT and FraudGPT have been developed, with the sole purpose of facilitating a full range of different cyber threats. Described as “ChatGPT with no Ethical Boundaries” by its developer, WormGPT is being sold on DarkWeb forums as a tool to aid in offensive operations. From generating phishing campaigns, developing malware, and the creation of deepfake content, artificial intelligence has been an impacting aid to threat actors, greatly in cutting down the time taken in practically any stage of the Cyber Kill Chain.
Internet of Things (IoT)
With an estimated 25.4 billion connected devices by 2025 following from the adoption of 5G (Statista, 2023), the cyber attack surface is also being supplied with new potential access points into a victim’s network. One of the biggest challenges introduced from IoT is the management of a constant stream of new devices being connected to the internet. Having these new devices incorporated into not just home, but business networks can make asset management an ever increasing, but key part, of cyber security to maintain. Being able to track devices connected to your network is critical to spot unusual behaviour and deal with security incidents. Having this regularly changing inventory, as well as the new data it is generating, can start to become unmanageable and make identifying those key baselines for normal activity much more difficult. A further management issue with IoT is patch management, an already complicated aspect of cyber security that can be difficult to maintain. With patch management being reliant on knowing devices and versions within your network, adding the complexity of IoT devices and their inherited vulnerabilities can open up further and unknown potential access points for an attacker.
Overall, the three examples above are just a few of the factors that contribute to cyber crime becoming more accessible to all types of computer users. The decrease in technical skill required to conduct cyber attacks is opening up the attack surface to more potential threats actors, with varying motivations, than what has been seen in previous years.
What have we seen this year?
Some of the notable ransomware incidents we have seen since the NHS 111 service cyber attack are noted below:
Royal Mail Ransomware Attack
In 2022 the LockBit ransomware group claimed responsibility against Royal Mail, forcing the company to stop its international shipping service after causing severe disruptions. The breach was confirmed after a LockBit affiliate accessed the company network and deployed the LockBit Black Ransomware payload to encrypt the network, steal data, and demand a ransom payment. Since the attack there is very little information into how the LockBit affiliate gained access to the Royal Mail network, however the most common LockBit initial access vectors are through phishing emails, exploiting publicly available applications, or exploitation of public RDP servers. The group added the company to their leak site and after weeks of negotiations no ransomware payment was agreed. The negotiation conversations were also leaked by the group which show the negotiation side we often don’t tend to see. Once the negotiations failed, the group then started to leak the company data.
Barts Health NHS Data Breach
During June 2023, an attack was conducted against the Barts Health NHS Trust, one of the UK’s largest hospitals. The group that claimed responsibility for the attack was the ALPHV/BlackCat ransomware group. It was reported that staff’s personal identities were compromised, which included financial details, passports, and driving licences. It is currently unknown if patient or medical data was stolen in the attack, with the group leaking staff data essentially to confirm that they had breached the network. The group conducted double extortion in this attack, meaning the attackers stole data and will release the data unless a ransom is paid before the deadline. It is reported that the attackers stole around 7TB of data. An interesting aspect to this attack is that it seems the ransomware group skipped the deployment of ransomware and opted for data exfiltration alone, allowing for operations to carry on as usual during the ransom period.
MOVEit Transfer Vulnerability
During June 2023 a ransomware group named ‘Cl0p’ started a campaign to exploit a zero day vulnerability in the file transfer tool, MOVEit. The group exploited the vulnerabilities to conduct mass data exfiltration with companies affected worldwide. This allowed the attackers to gain unauthorised access to MOVEit transfer servers to deploy webshells resulting in the theft of sensitive data. A large number of UK companies were affected by this attack campaign, which saw a still unconfirmed number of staff and company data stolen, with companies still being added to the Cl0p ransomware group’s leak site. The current UK companies affected by the breach include the BBC, British Airways, Boots, JD Sports, and the University of Manchester. It is likely more may be affected during the coming months. Once organisations were added to the leak site, they had a certain amount of time to pay a ransom to have their data deleted. Organisations that passed this deadline saw their data leaked by the attackers.
Ransomware Targeting ESXi
An overall trend observed in the ransomware industry is a renewed focus on targeting VMware ESXi servers. VMware ESXi is a Virtualisation Software that a vast number of organisations use, and has previously been predominantly overlooked in ransomware attacks. However, throughout 2023, several ESXi specific encryptors have emerged. Some examples of these are ESXiArgs, Akira, and RTM Locker, the former of which was developed solely to target unpatched ESXi servers. This is a huge cause for concern, as large swathes of infrastructure are often hosted on ESXi, which could all be compromised with a single infection. This highlights the importance of ensuring that ESXi servers, and other infrastructure are properly segregated from the internet, and patched kept up to date.
Conclusion on the Ransomware Attacks
In conclusion, ransomware attacks against healthcare providers worldwide are more prevalent than ever before, with healthcare continuing to be in the top 10 most targeted industries for ransomware attacks. Ransomware can have a devastating impact on networks, especially healthcare networks, causing critical medical procedures to be cancelled, affecting emergency phone lines, and communication systems. Depending on the backup, patching and asset management policies of organisations, system recovery could take weeks, perhaps months to fully implement and recover from a ransomware attack. Whilst understandably difficult to maintain, with the introduction of new technology and threats emerging, there are a number of ways organisations can mitigate threats against cyber attacks. Still one of the most common initial access vectors is the use of phishing emails; having users take part in regular phishing exercises and spreading user awareness can be massively beneficial. In some instances we have seen, healthcare organisations have been compromised by attackers exploiting publicly available infrastructure. Having devices, especially IoT devices, exposed could have drastic consequences if they have not been configured correctly. Limiting these applications and devices to only certain IP address ranges to access can mitigate threat actors from exploiting these public facing assets. Admins should consider patching public applications and devices as priority to mitigate exploit campaigns and to protect infrastructure. It is important to note that it is not just healthcare providers that can fall victim to these attacks as we have discussed. By following and implementing good sources of cyber security guidance, such as the NCSC, organisations can limit their likelihood of becoming a victim to ransomware and greatly lower its impact if such an incident did take place.
 Cybersecurity
Cybersecurity 




