Reminder: Cyber Threat Intelligence
Cyber threats are continuously growing in complexity and frequency, therefore the ability to rapidly process and act upon Cyber Threat Intelligence (CTI) can mean the difference between a mitigated threat and a breach. In the first part of our CTI focused blog posts series, we introduced the Intelligence Production Cycle and proposed a functional and technical architecture for a Cyber Threat Intelligence platform integrated into and supporting both SOC and Incident Response (IR) operations. The second part centred on how Cyber Threat Intelligence can contribute and support the SOC’s Threat Hunting and Detection Engineering activities through a targeted Threat Actor Intelligence activity. In this third part, we will focus on this paramount stage of ‘Collection’ within the Threat Intelligence cycle, how we at Airbus Protect are enhancing this stage with Artificial Intelligence (AI), and some of the ways we see this being adopted in the constantly evolving Cyber Threat Intelligence landscape.
What is Intelligence Collection?
The collection phase in the intelligence lifecycle is a crucial step where raw data is gathered from various sources to answer specific intelligence requirements. This phase is designed to acquire the information that will later be analysed and processed to support decision-making, policy formation or security measure implementation. The primary goal is to gather relevant and actionable data from a variety of sources, ensuring that it directly supports the intelligence needs or objectives set in the earlier stages of the lifecycle (such as during the planning and direction phase). Ensuring the data is comprehensive, relevant and reliable for future analysis.
Types of Collection in CTI
The gathering of Cyber Threat Intelligence initially requires the identification of the sources. There are several methods or sources that can be used for collecting intelligence, some of which are described below:
- HUMINT (Human Intelligence): Information gathered from human sources, such as informants, interviews, or undercover operations.
- SOCMINT (Social Media Intelligence): Information collected from an aggregation of social media platforms.
- ISAC (Intelligence Sharing and Analysis Centre): Intelligence derived from non-profit organisations that provide a central resource for gathering information.
- OSINT (Open Source Intelligence): Information from publicly available sources, like newspapers, social media and online databases.
- MISP (Malware Intelligence Sharing Platform): An open source Threat Intelligence platform used for sharing indicators of compromise.
- Dark Web Marketplaces and Forums: Marketplaces usually used for cybercrime activity such as the sale of stolen data, malware services and tools and compromised user credentials.
In order to successfully collect from this vast range of sources, an effective collection plan needs to be put in place. This involves intelligence analysts defining the specific information requirements that must be met as part of their overall outcome. This could involve focusing on a particular customer, region, target, or product. The collection plan also outlines the logistics of the phase such as how and where the data will be gathered, the resources and methods to be used, and who will be responsible for each collection activity.
What challenges do CTI experts face when they do Intelligence Collection?
As anticipated with such a vast amount of data, the intelligence collection phase can be faced with various challenges, which can impact the overall effectiveness of the intelligence cycle. Some of the main problems with the process of collection in the intelligence cycle include:
- Volume of Data
The sheer amount of data collected can be overwhelming. With the explosion of digital information (social media, open-source intelligence, surveillance data, etc.), CTI teams may face difficulties in sorting through massive amounts of information to find relevant data.
This can also leave important intelligence buried under an avalanche of irrelevant or trivial information, making it harder to identify actionable insights.
- Reliability and Accuracy of Sources
Not all intelligence sources are equally reliable, and there can be challenges in validating the authenticity of the information. Some sources may be biased, misinformed, or deliberately deceptive. Unreliable sources can lead to false conclusions, which can influence decisions that affect a customer’s security or operations.
- Access to Information
Some critical information might be inaccessible due to technological limitations, political barriers, legal constraints, or secrecy. Additionally, information may be intentionally concealed by adversaries or withheld due to internal policies. Limited access to key intelligence can hinder decision-making, preventing an accurate picture of the situation from emerging.
- Data Overload and Analysis Paralysis
Intelligence agencies may face a situation of “analysis paralysis” where they gather so much information that they struggle to make sense of it all. This can happen when there are too many conflicting or ambiguous pieces of data. Slow or poor decision-making, as analysts become bogged down in trying to process and prioritise the collected data.
- Timeliness
Intelligence collection needs to be timely to be useful, especially in fast-moving industries such as cybersecurity. However, the time it takes to collect and process intelligence can lead to delays. Delays in gathering intelligence can result in missed opportunities or response time lag, allowing threats to evolve rendering the original intelligence to be quickly redundant.
- Security and Encryption Challenges
As intelligence collection becomes increasingly digital, securing communications and data becomes more difficult. Cyber threats, hacking, and leaks can undermine the collection process and also make the community in general less willing to share with their fellow security professionals. Adversaries may use cyber attacks to disrupt or deceive the intelligence cycle.
- Legal and Ethical Issues
Collection efforts often need to balance national security interests with privacy and human rights. There can be legal limitations on the collection of data, in some cases these legal constraints can prevent the collection of certain types of intelligence, reducing the breadth and depth of the intelligence gathered.
- Human Factors and Bias
As hard as they may try not to, analysts and agents involved in the collection process can introduce their own unconscious biases, either through personal opinions or pre-existing beliefs, into the collection process. Biases can distort the selection and interpretation of data, potentially leading to inaccurate intelligence and flawed conclusions.
- Cost and Resource Constraints
Collecting high-quality intelligence, especially through human intelligence (HUMINT) or technical means (SIGINT, IMINT, etc.), requires significant resources in terms of personnel, technology, and funding. Insufficient resources or budget constraints can limit the effectiveness and consistency of intelligence collection, leading to gaps or inefficiencies.
Organisations have to retain visibility of existing, emerging and evolving cyber threats, implement appropriate proactive and reactive measures, as well as define effective mitigation strategies. The collection phase of the intelligence cycle is essential to this, as the data gets transformed into information and ultimately intelligence, the sheer volume of outputs drops significantly; but the value added from the output increases exponentially, as pictured in the figure below:
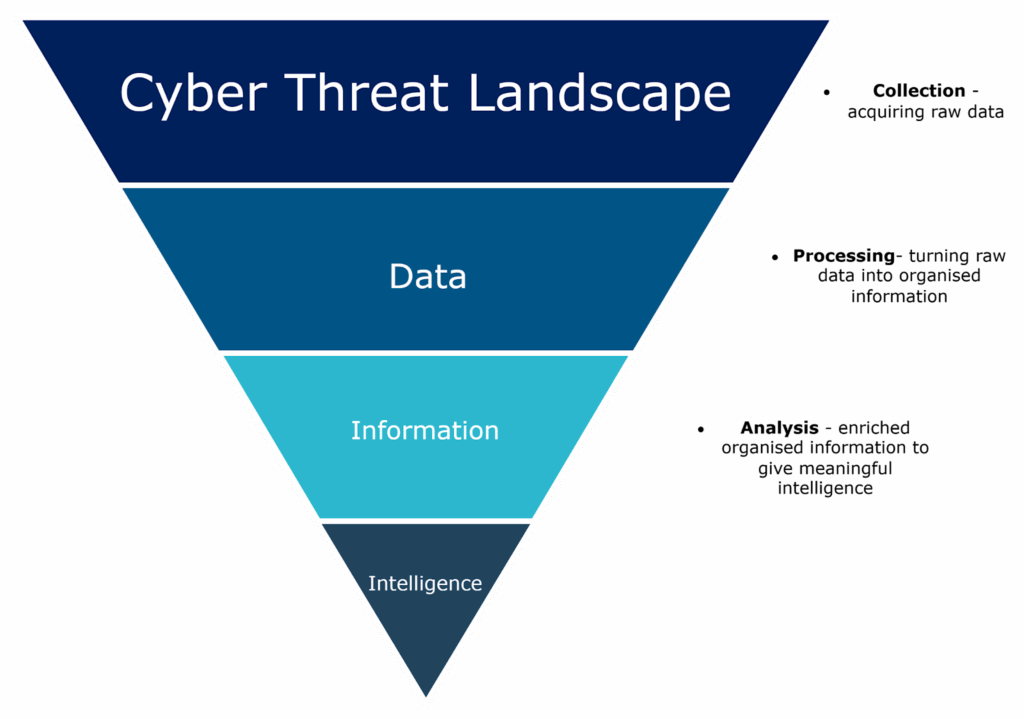
However, addressing the collection phases inherent issues requires careful planning, investment in technology, and ongoing evaluation of methods and processes to ensure that the intelligence cycle remains effective and responsive to the ever-evolving nature of threats and adversaries.
Intelligence Collection Models
There are several models and frameworks that can help with the collection phase and some of the previously mentioned challenges of the intelligence lifecycle. These models and frameworks are designed to streamline the collection process, improve efficiency, and ensure that the intelligence gathered is both relevant and actionable. Below are just some of the key models and frameworks:


