Don’t let a crisis disrupt your business. Our comprehensive approach starts with cyber resilience with proven expertise in crisis management and business continuity to ensure a secure future for your organisation. We can address all your risk management needs, which are not limited to cybersecurity.
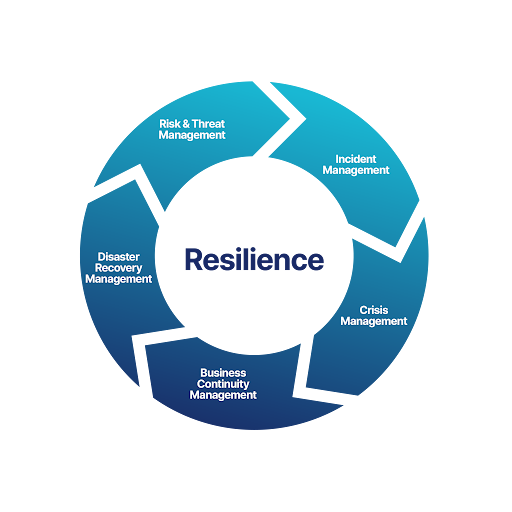
Cyber resilience is a key component of business resilience. It represents an organisation’s ability to anticipate, resist, detect, respond to and quickly recover from cyber attacks or IT incidents.
The objective is to maintain the continuity of your essential activities, limit the impact even in crisis situations, and subsequently go beyond cyber resilience to achieve comprehensive resilience for your activities.