What is vulnerability management?
Vulnerability management has become indispensable for large organisations. It’s not a one-off cybersecurity action, but rather a continuous cycle of prevention, detection, remediation, and monitoring that adapts a company’s defenses to evolving threats. Airbus Protect’s Threat Management Centre (TMC) team categorises vulnerability activities into two distinct areas: passive vulnerability management and active vulnerability management.
Passive Vulnerability Management
Passive vulnerability management enables us to identify and address vulnerabilities impacting the project components we monitor. When a security vulnerability is deemed relevant, our team drafts a security bulletin for clients, detailing affected components, necessary patches, and the severity level for the project. This is considered passive vulnerability management because it’s not a proactive monitoring approach, and we don’t scan assets ourselves.
Before issuing a security bulletin, our team waits for a vulnerability to be listed by a vendor (Microsoft, Cisco, Red Hat, etc.) or by authorities (e.g., CERT-FR, CISA, NIST).
Aggregating Collected Information
Our cross-functional working group, COBRA, comprises vulnerability and intelligence specialists who play a crucial role in centralising vulnerability information to identify emerging threats. COBRA retrieves technical data from specialised sources, vulnerability databases, and cyber intelligence feeds. Our toolset allows for automated monitoring of hundreds of information sources, including specialised blogs, security websites, and official publications. Finally, the passive vulnerability team supplements this with manual research and monitoring of non-automated channels.
All this data is then aggregated into a centralised platform, analysed, and correlated to filter relevant information, identify critical vulnerabilities, and provide contextualised alerts to security teams. This approach ensures a comprehensive, near real-time view of the threat landscape, while prioritising actions based on the risk level and criticality of the affected assets.
Creating and Updating Security Bulletins
When a security flaw is relevant, team members draft a security bulletin for clients, explaining in detail which components are impacted, which patches need to be installed, and the criticality level for the project. Bulletins are then regularly updated to reflect evolving knowledge: patch releases, new active exploits, changes in impact analysis, etc. This keeps security teams informed with the latest information, allowing them to prioritise their actions effectively.
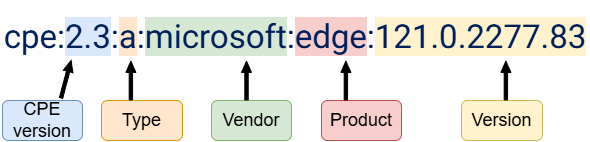
CPE (Common Platform Enumeration) is a standardised identifier used to precisely describe software, operating systems, or hardware affected by a vulnerability. When creating or updating an ADSC bulletin, it’s essential to include the associated CPEs. This enables automated linking of vulnerabilities to assets within an organisation’s infrastructure via vulnerability management tools.
By integrating accurate and relevant CPEs, the ability to automatically detect vulnerable systems is significantly enhanced, which accelerates the identification of areas needing remediation and strengthens the relevance of generated alerts.
 Cybersecurity
Cybersecurity